1. Overview
Plannerly supports Microsoft Entra ID (Azure AD) as a simple and secure sign-in option. Your team can authenticate using their Microsoft work accounts.
To enable Microsoft Login for your organization, you only need to create an App Registration in your Microsoft Entra tenant and add one redirect URL.
2. Create an App Registration
Follow these steps in your Microsoft Entra Admin Center:
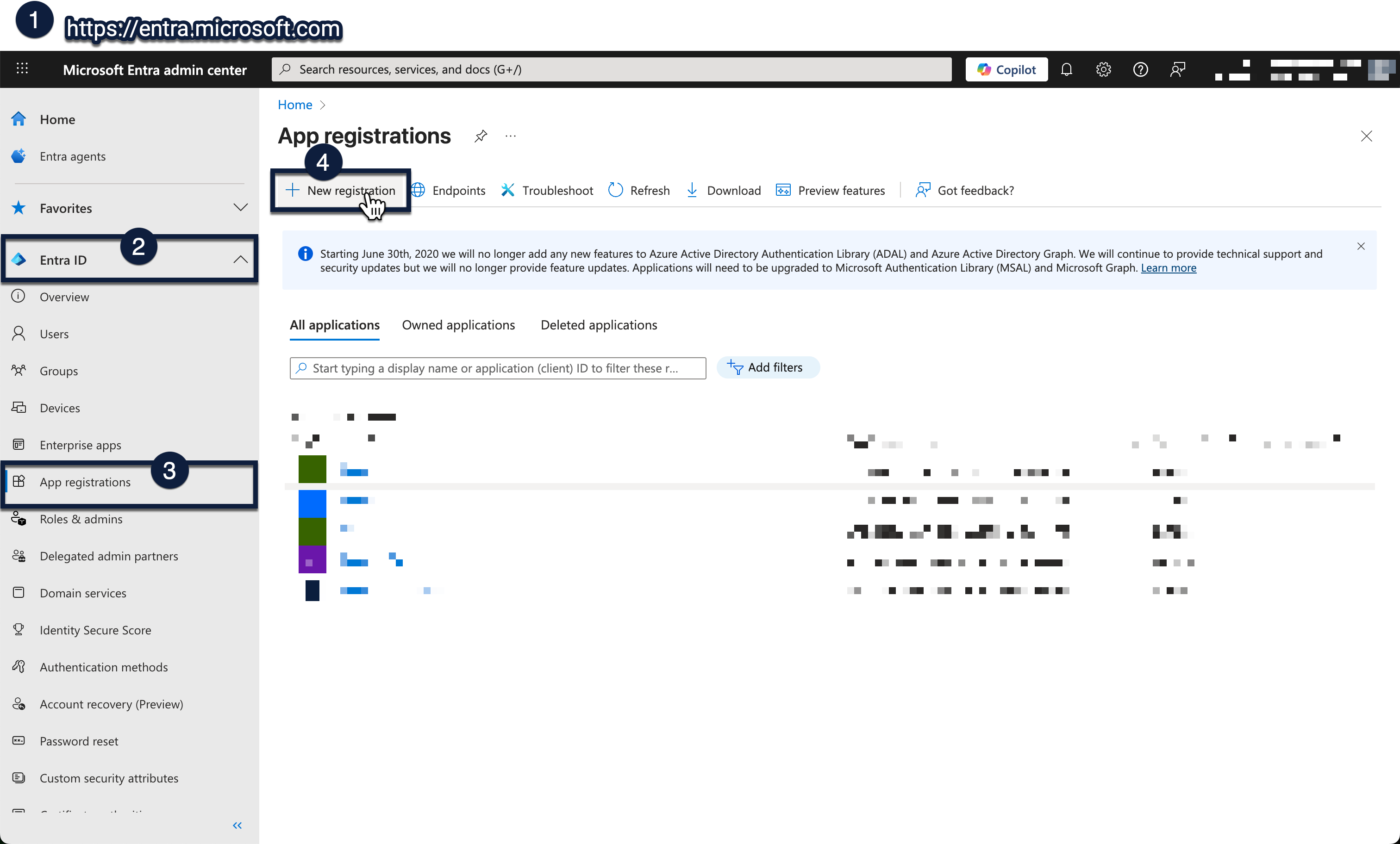
- Go to https://entra.microsoft.com
- In the left menu, open Entra ID
- Select App registrations
- Click + New registration
- Name the app: Plannerly
- Under “Supported account types”, choose:
Accounts in this organizational directory only - Scroll down to Redirect URI - select "Web" and enter:
https://app.plannerly.com/
- Click Register
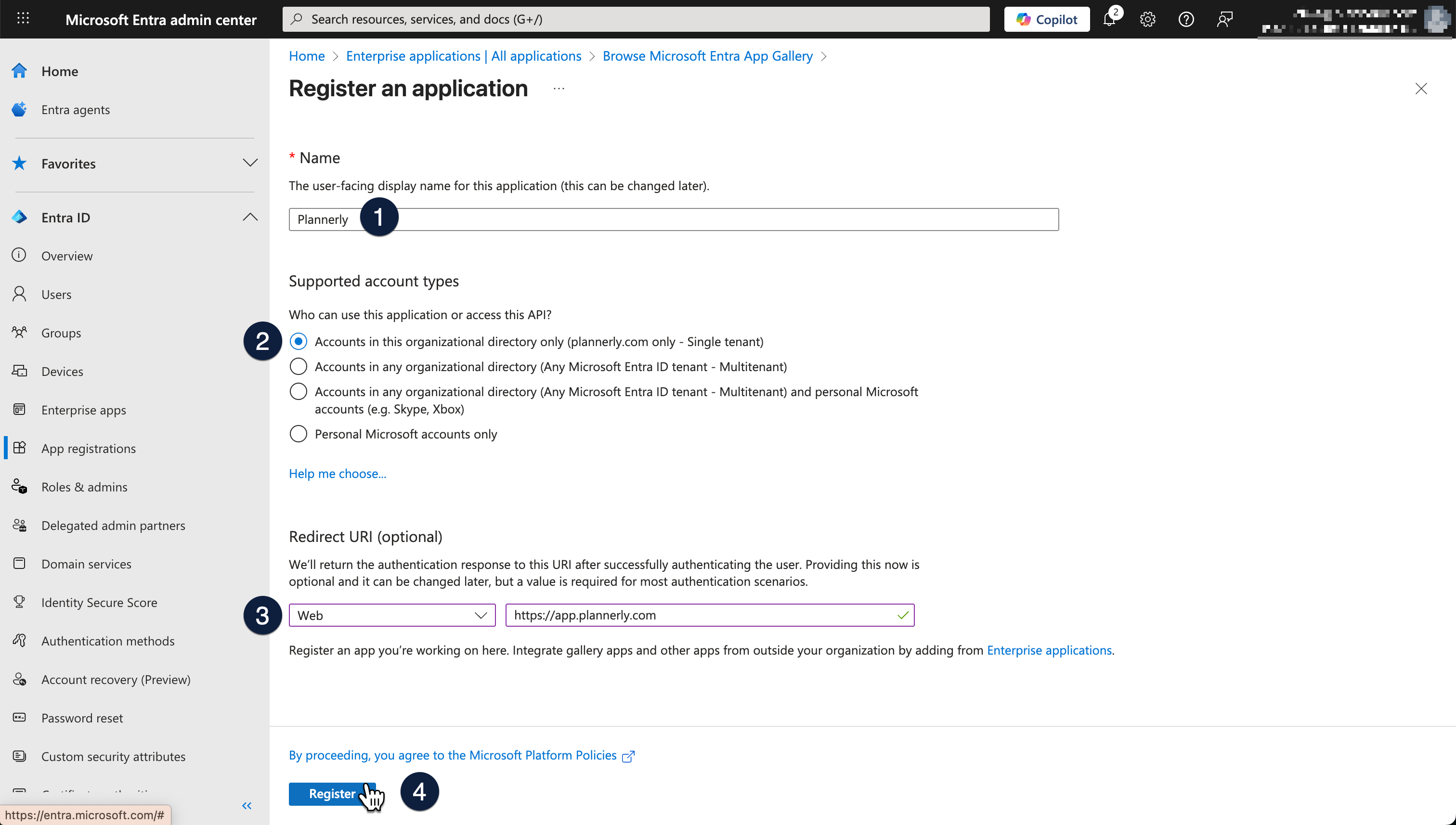
Your App Registration is now created. Microsoft will automatically generate a corresponding Enterprise Application for user assignment and access control.
3. Assign users who can sign in to Plannerly
Since the Enterprise Application is created automatically, assign users like this:
- Go to Enterprise applications in Entra.
- Search for your app name (Plannerly)
- Open it, then select Users and groups
- Click + Add user/group
Choose all the users or groups who can sign in to Plannerly.
A quick heads-up: we suggest letting everyone in your company log in. This just helps avoid any future headaches for employees trying to get access!
Click Assign
Users assigned here will be able to log in to Plannerly using their Microsoft work accounts.
4. Restrict your domain to Microsoft SSO only
Plannerly will enforce that users from your organization must use Microsoft SSO and cannot log in through other methods.
This domain restriction:
- forces Microsoft Login for your domain
- blocks login through manual passwords, Google, Autodesk, Procore, and all other methods
- ensures only users you assign in Microsoft Entra can access Plannerly
How to request your domain restriction
A Plannerly Administrator must email:
📧 security@plannerly.com
Please include:
- Your company name
- The domain(s) to restrict (example:
company.com) - The SSO method to enforce: Microsoft
5. Authentication flow
- You create a Plannerly App Registration in Microsoft Entra.
- You assign users or groups to the Plannerly Enterprise Application.
- Plannerly restricts your domain to Microsoft SSO.
- A user goes to Plannerly and chooses Log in with Microsoft.
- Microsoft authenticates the user and checks your Entra permissions.
- If allowed, Plannerly logs the user in.
6. Troubleshooting
6.1 User is told they must use Microsoft to sign in
The domain restriction is active. The user should:
- Click Log in with Microsoft
- Use their company Microsoft account (not a personal email)
6.2 User cannot log in even with Microsoft
Check the following:
- The user is assigned in Enterprise applications → Plannerly → Users and groups
- The user belongs to your Microsoft Entra tenant
- The user is using the same email domain added to the domain restriction
- No Conditional Access policy is blocking the Plannerly app
If the issue continues, ask your Plannerly admin to email:
6.3 Admin cannot find the Plannerly Enterprise Application
- Search under Enterprise applications (not App registrations)
- Check for slightly different naming (e.g., “Plannerly SSO”)
- If missing, re-create the App Registration for Plannerly
7. Summary
- Create a Plannerly App Registration in Entra
- Add the redirect URI
https://app.plannerly.com/ - Assign users via Enterprise Applications
- Ask Plannerly to enforce Microsoft-only login for your domain





